Tuesday, December 30, 2008
Fake Windows Media Player Flaw
Source: DarkReading.com
Tuesday, November 11, 2008
Cyber-Extortion: A Review
 Cyber-Extortion is the use of computers and communication systems to obtain or attempt to obtain unauthorized access to money or financial gain by threat. Cyber Extortion is so common in the information security arena that it doesn't raise the same attention as in the past.
Cyber-Extortion is the use of computers and communication systems to obtain or attempt to obtain unauthorized access to money or financial gain by threat. Cyber Extortion is so common in the information security arena that it doesn't raise the same attention as in the past.There are various forms of cyber-extortion, but in general if the hacker’s demand is not met, than an adverse event will occur to the victim or company.
Just recently, Express Script became a victim of a cyber-extortion attack from an incident that occurred in early October of 2009. Express Script received a letter claiming that the company's network had been breached and threatening to release millions of customer records unless the firm paid money to the thieves. The letter listed personal information on 75 of Express Script's members, including their names, dates of birth, social security numbers, and in some cases, their prescription information, the company stated. Express Scripts added that it had reported the crime to the FBI, which is currently investigating.
Often companies will just pay the cyber-extortionist in hopes of having the matter go away without public knowledge. This is due to being penalized by federal regulators, having to notify customers of the matter, the process of conducting damage control, the cost in resolving the matter and losing customer confidence in that industry.
Below are some major cyber extortion events that has occurred world-wide. These were obtained from www.acapsecurity.com:
Barclays Bank, a major international bank, was broken into by a cyber-criminal whose attack focused on the bank's Barclaycard division, which with 8 million cardholders is Europe's largest credit card system. Allegedly the attack included the theft of credit card numbers and valuable customer information, with law enforcement reporting the cyber-criminal did make a $25 million extortion demand on Barclays Bank. The matter is before the courts in London.
Guardian, Oct 19, 2001. Underline added.
A cyber-thief from Kazakhstan broke into the computer networks of the Bloomberg financial news service owned by Michael Bloomberg the current Mayor of New York City. Thereafter the thief became a Cyber-Extortionist by demanding an extortion payment.
U.S. Attorney's Office Press Release, Aug 14, 2000. Underline added.
A cyber-thief broke into the computer networks of Parametric Technology Corporation and thereafter made an extortion demand for $1 million plus $40,000 per month.
St. Petersburg Times, Aug 24, 2000. Underline added.
The Secret Service and the FBI reported that a cyber-criminal had broken into the computer system of Online Resources, a company that offers online banking, electronic payments and other financial services to 525 financial institutions in the U.S. The cyber-thief as part of the attack stole customer records that included names, addresses and bank account numbers. The theft was followed by an extortion demand on at least one bank.
InfoSec News, Feb 8, 2002. Underline added.
On August 21, 2001 a cyber-thief broke into a unit of Ecount, an electronic payment company and allegedly stole 350,000 credit card numbers and thereafter made an extortion demand on the company.
ZDNet News, Oct 11, 2001. Underline added.
Two Russian cyber-criminals broke into hundreds of computer systems, stole sensitive client and financial information and then made extortion demands on the victimized companies.
InfoSec News, Oct 18, 2001. Underline added.
Cyber-criminals broke into the British division of Visa, the major credit card company, and stole data. Visa claims the stolen data was useless information. Obviously the cyber-criminals believed the data was valuable as they made an extortion demand on Visa for approximately $14 million U.S.
InfoSec News, Jan 20, 2000. Underline added.
A cyber-criminal made an extortion demand on CD Universe, an Internet music retailer, claiming he had stolen as many as 300,000 credit card numbers. The alleged cyber-extortionist was suspected of operating from a base in Eastern Europe. On Christmas day the cyber-criminal began posting more that 25,000 of the allegedly stolen card numbers on a web site. Thousands of customers who had shopped at CD Universe cancelled their credit cards.
Mercury News, Jan 26, 2000. Underline added.
A cyber-criminal from Russia broke into one of the New York bank's computer systems stole confidential customer information and extorted money for not releasing the customer information.
Associated Press, Jan 24, 2002. Underline added.
Types of Wireless Attacks
 Standard wireless communication occurs when the end user and the wireless access point are able to communication on a point-to-point basis without interruptions. There are many attack variations in existence against wireless networks that breaks the standard communication format. These attacks includes the denial of service attacks, the man in the middle attacks and the WEP key-cracking attack to name a few and are described below.
Standard wireless communication occurs when the end user and the wireless access point are able to communication on a point-to-point basis without interruptions. There are many attack variations in existence against wireless networks that breaks the standard communication format. These attacks includes the denial of service attacks, the man in the middle attacks and the WEP key-cracking attack to name a few and are described below.Denial of Service (DoS) attacks
The objective of a Denial of Service (DoS) attack is to prevent authorized users access to legitimate network resources by denying them service. A DoS occurs when the malicious attacker sends an abundant of garbage data to the wireless access point choking all other communications to legitimate users.
Man-in-the-middle attacks
A man-in-the-middle attack consists of a malicious user (hacker) inserting themselves into the data path between the client and the AP. In such a position, the malicious attacker can delete, add, or modify data. The man-in-the middle attack also enables the malicious attacker access to sensitive information about legitimate users such as username and passwords, credit card numbers and social security.
War driving
Wardriving is the mapping of wireless access points (WAP) by driving or walking through populated areas carrying wireless equipment such as a laptop or a PDA to detect active wireless access points. The tools used for this are available freely off the Internet in the form of Netstumbler and Ministumbler (http://www.netstumbler.com/). Once the malicious attacker located vulnerable wireless access points, they are able to mount attacks to other locations under the cover the compromised network.
Wired Equivalent Privacy (WEP)
The Wired Equivalent Privacy (WEP) authentication consists of each frame being encrypted as it is transmitted to the wireless access point. WEP possess many deficiencies such as the ability to be compromised within a short period of time. Hackers can fairly easily decode WEP-encrypted information after monitoring an active network for less than one day. An application such as WEPCrack (wepcrack.sourceforge.net/) is a freely available tool often used to implement such an attack.
Wednesday, May 28, 2008
New Adobe flaw being used in attacks
Thursday, May 22, 2008
Why Bots are Bad News to your Network…

Adhering to company policies such as remote access, software downloads and patch management are all key to protecting the enterprise.
Thursday, May 15, 2008
Webcast: Safeguarding Critical Data

I sat through an interesting webcast today on safeguarding critical data. Below is a description of the webcast and access to access the webcast, click here.
Topic: Safeguarding Critical Data
Availability: Now on-demand
Speakers:
Howard Schmidt,
President/CEO, R & H Consulting
Rich Baich
Principal, Deloitte and Touche
Bob Flinton
VP Product Marketing, netForensics
Moderator:
Illena Armstrong
Editor-in-Chief, SC Magazine
Join former US Cybersecurity Chief Howard Schmidt and Deloitte and Touche's Rich Baich as they present best practices for safeguarding your critical data! View the webcast now> (no form required)
A huge issue for all organizations today is the threat of data theft or exposure. The multitude of data breaches in the news confirms the growing incidence of electronic fraud, insider threat, sabotage and unauthorized access.
SC Magazine brings together two of the security industry's most renowned experts along with netForensics in this new webcast, Safeguarding Critical Data, to discuss:
*
Key aspects of data protection that are overlooked
*
Important considerations for audit and compliance
*
Proven tactics for identifying malicious behavior
*
6 considerations for your data protection program
This collaborative webcast includes best practices for implementing a risk-based approach to compliance, and guidance for developing your own data theft program roadmap.
Wednesday, May 7, 2008
The Benefits of Virtualization and How to Conduct Data Protection
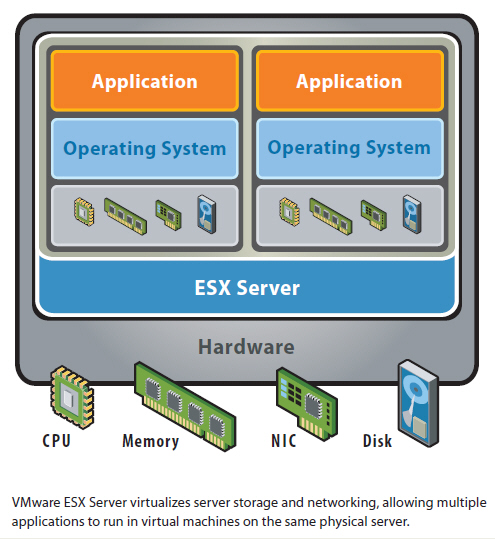 Hardware consolidation and reduced energy bills are some of the cost benefits of virtualization. The ease of use and the snapshot functionality are some of the technical benefits of virtualization. As more organization initiate virtualization technology and more critical systems begin to reside on them, security will become vital issue.
Hardware consolidation and reduced energy bills are some of the cost benefits of virtualization. The ease of use and the snapshot functionality are some of the technical benefits of virtualization. As more organization initiate virtualization technology and more critical systems begin to reside on them, security will become vital issue. Below are some key ideas to implement on your virtual system solutions. For the full list of suggested security features and their explaination as it relates to virtualization security, please go to SecurityOrb.com at www.securityorb.com
Virtualization Security Features:
· Update your operating systems and the applications
· Install and update antivirus on virtual machines and the host
· Firewall each virtual machine from each other.
· Isolate each virtual machine from each other and the host
Click here for more in this post
What is your virtualization experience? Tell us...
Tuesday, May 6, 2008
Port Scanning: The Forgotten Danger before the Attack
 This excerpt has been taken from an upcoming article that I just completed on Portscanning. For anyone in information security and security monitoring, portscans are common and often ignored due to its frequency and volume.
This excerpt has been taken from an upcoming article that I just completed on Portscanning. For anyone in information security and security monitoring, portscans are common and often ignored due to its frequency and volume.I have worked at organizations were we observed over a million scanning events a day. Often I hear other security professionals state, they block these scanning events from their monitoring stations since it is external to their network and a recourse strain on operations.
The problem with that approach is the lost of visibility to malicious event knocking on the door of the network.
Port Scanning: The Forgotten Danger before the Attack
A port scanner is a tool designed to search for open ports on systems connected on the network. This tool can be used by network and security professionals to perform legitimate functions to secure their systems and can be used by malicious users to begin staging an attack. There are two of scanning functions, the first is called a port scan. In a port scan, the scanner listens to all ports on a single host to determine which ports are available. The second type is called a portsweep. A portsweep is conducted on multiple hosts on a network looking for all available ports on all accessible systems.
Thursday, March 20, 2008
Classified Information Classification

Classified Information Classification
I’ve often looked at the technological aspects of information security, but from some recent events, I will be spending the next few days focusing on some non-technical function of information security and protecting information assets.
Classified information can be categorized in these three areas, top secret, secret and confidential.
Their descriptions are listed below:
Top Secret – The unauthorized disclosure of information can be expected to cause grave damage to national security.
Secret – The unauthorized disclosure of information can be expected to cause serious damage to national security.
Confidential – the unauthorized disclosure to information can be expected to cause damage to national security.
A person can access classified information provided that a favorable determination of eligibility for access has been made by an agency (Clearance), the person has a signed and approved nondisclosure agreement and the person has a “need-to-know” to access the information.
This is a very serious process and necessary to access classified information.
Tuesday, March 11, 2008
Safari Web Browser and Online Fraud
Safari Web Browser and Online Fraud
PayPal says no…
By Kellep A. Charles
Published on March 11, 2008, 12:38 AM EST
PayPal the leading e-commerce business allowing payments and money transfers to be made through the Internet recently did not recommend Apple’s Safari web browser when conducting tractions on their website. Safari currently does not have two very important anti-phishing security features that detects and prevents online fraud to occur. Internet Explore 7, Firefox 2 and Opera do have these critical anti-phishing features and have made the PayPal recommended list.
Michael Barrett, Chief Information Security Officer at PayPal stated, “Apple, unfortunately, is lagging behind what they need to do, to protect their customers”.
My recommendation to Mac OS X user on protecting yourself from online fraud is to not use Safari until Apple adds the anti-phishing capabilities. Even though Safari is the default web browser on the Mac OS X platform, Firefox and Opera are viable solutions.
Send an email to Apple and tell them to get on the ball…
Wednesday, March 5, 2008
Child Safety on the Internet
 The Internet has made it possible for people to communicate with anyone anywhere in the world. That is a scary thought when it comes to thinking about child safety on the Internet. On a daily basis, kids are on line communicating on chat rooms without adult supervision not really knowing the person on the end is who they claim to be.
The Internet has made it possible for people to communicate with anyone anywhere in the world. That is a scary thought when it comes to thinking about child safety on the Internet. On a daily basis, kids are on line communicating on chat rooms without adult supervision not really knowing the person on the end is who they claim to be.In the real world, we tell kids not to talk to strangers; the same idea needs be enforced when it comes to using the Internet if not more so… The numbers of predators and the anonymity they are able to obtain make the matter just that much more dangerous.
Some of the difficulties parents are facing deals with education and technology. When it comes to technology, kids are usually ahead of their parents in the computing knowledge. Many of their activities such as chatting and online video conferences are easily hidden from the parents. Then you have the parents that do apply some form of security or privacy controls such as content filters for protect to only have them bypassed the kids.
It is a well-known fact that kids talk about way to bypass the controls put in place to protect them.
Of the most victimized group of Internet
Teenage girls are most often victimization of all the groups. Some of the techniques used by an online predators are to:
1. Use seduction techniques
2. Try to win their confidence
3. Go after problem kids
4. Go after kids with low self-esteem
5. Go after kid with very little friends
The Internet predator will play with their emotions so the child will think this person understands them and be more open to further a relationship.
To report any suspicious activities, one of the best resources I can recommend is:
“The National Center for Missing and Exploited Children” at www.missingkids.com.
They have law enforcement, state and federal agencies that can assist with these matters.
Some tips that should help in protecting our kids:
1. Tell them to never give any personal information of any kind, make a list of questions that should not divulge.
2. Educate yourself and monitor what your kids are doing.
3. Pay attention to their Internet usage, if they are spending more time on the Internet than eating, playing or talking to friends, then something may be going on.
Wednesday, January 30, 2008
File Sharing Applications: Another way to be a victim of identity theft
 If you are using a peer-to-peer file sharing program to download music and videos, you may be a prime candidate for Identity Theft. Applications such as Limewire, Edonkey and numerous others on the Internet may also allow individuals to download personal documents from your computer at will. The issue stems from the sharing of the “My Documents” folder as the default folder for sharing media. Most users and file sharing applications will select the “My Documents” folder because that is where most of the media files are located. But think about it... what else do you have in the “My Documents” folder? Family Pictures, Personal Documents and etc...
If you are using a peer-to-peer file sharing program to download music and videos, you may be a prime candidate for Identity Theft. Applications such as Limewire, Edonkey and numerous others on the Internet may also allow individuals to download personal documents from your computer at will. The issue stems from the sharing of the “My Documents” folder as the default folder for sharing media. Most users and file sharing applications will select the “My Documents” folder because that is where most of the media files are located. But think about it... what else do you have in the “My Documents” folder? Family Pictures, Personal Documents and etc...To date, I have read and heard of individuals accessing mortgage applications, loan paper work and even 1040 tax information with the social security numbers of a whole family.
My recommendation if you do insist on using a file sharing program is to create a folder where the sharing can take place such as “Shared Documents” and do not place any personal information in that folder.
Security Product Review: Nessus Vulnerability Scanner by Tenable
From time to time, I will be conducting product reviews of a security tool, application or website that I find to be very useful.
As a System Security Assessor, I often use and test many different tools and applications to do my job. One that has amazed me in recent years with excellent performance and results is the Nessus Vulnerability Scanner by Tenable.
 Nessus is a free program designed to automate the testing and discovery of known security problems on the network and computer systems. For a free tool, Nessus has many useful capabilities such as using the Nessus Attack Scripting Language (NASL), which allows security professionals to use a simple language to describe individual attacks in conjunction to the provide vulnerability database based on the Common Vulnerabilities and Exposures schema. Another powerful feature of Nessus is the client server technology that allow for distributive architecture. The server portion runs on most flavors of Unix and Linux including the Mac OS X operating system while the clients are available for both Windows and Unix/Linux.
Nessus is a free program designed to automate the testing and discovery of known security problems on the network and computer systems. For a free tool, Nessus has many useful capabilities such as using the Nessus Attack Scripting Language (NASL), which allows security professionals to use a simple language to describe individual attacks in conjunction to the provide vulnerability database based on the Common Vulnerabilities and Exposures schema. Another powerful feature of Nessus is the client server technology that allow for distributive architecture. The server portion runs on most flavors of Unix and Linux including the Mac OS X operating system while the clients are available for both Windows and Unix/Linux.In my testing of Nessus against the more expensive commercial applications such as Foundstone’s Foundscan Security Scanner version 5 and Internet Security Scanner (ISS), Nessus faired much better than ISS in respects to initial setup, time of completion and less false positives. Against Foundscan, Nessus fell a little short in the scanning options and reporting.
My conclusion, for the price and results, Nessus is an excellent primary or secondary tool to use for your security needs. Tenable also offer support at a cost for those who needs it. Check it out and decide for yourself. You can find more information on Nessus at:
www.securityorb.com or www.nessus.org
Thursday, January 24, 2008
The Computer Information Systems Auditor (CISA) Certification
I recently sat for the Certified Information Systems Auditor (CISA) certification exam in December of 2007. We were told that the results from the exam will take about 8 weeks to come back to let us know if you have pass it or not.

This CISA certification is extremely popular with over 30,000 certified security professional from all over the world. The CISA certification exam is offered once per year at multiple testing locations worldwide and allows those who need to display knowledge of IT auditing, security, and control to set them at a higher level in the industry.
The CISA certification test your knowledge of the six core competencies:
1. The IS Audit Process
2. Protection of Information Assets
3. IT Governance
4. Systems and Infrastructure Life Cycle Management
5. IT Service Delivery and Support
6. Business Continuity and Disaster Recovery
The exam is four hours long consisting of 200 multiple-choice questions. A person aiming to obtain the CISA certification must show five years of verifiable experience in IS auditing, control or security is required, agree to the ISACA code of ethics and agree to adhere to the Information Systems Auditing Standards as adopted by ISACA.
The cost of taking the exam for ISCA members ranges from $300 to 385 depending upon when you register and if you do so online and $420 to 505 for non-members.
I will let you know status once my results are in…







