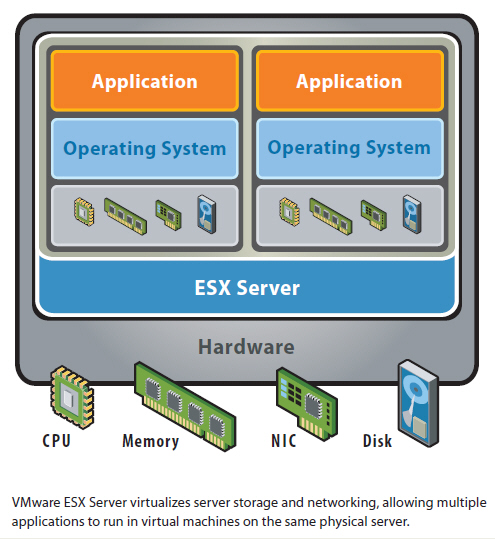
 Hardware consolidation and reduced energy bills are some of the cost benefits of virtualization. The ease of use and the snapshot functionality are some of the technical benefits of virtualization. As more organization initiate virtualization technology and more critical systems begin to reside on them, security will become vital issue.
Hardware consolidation and reduced energy bills are some of the cost benefits of virtualization. The ease of use and the snapshot functionality are some of the technical benefits of virtualization. As more organization initiate virtualization technology and more critical systems begin to reside on them, security will become vital issue. Below are some key ideas to implement on your virtual system solutions. For the full list of suggested security features and their explaination as it relates to virtualization security, please go to SecurityOrb.com at www.securityorb.com
Virtualization Security Features:
· Update your operating systems and the applications
· Install and update antivirus on virtual machines and the host
· Firewall each virtual machine from each other.
· Isolate each virtual machine from each other and the host
Click here for more in this post
What is your virtualization experience? Tell us...








